Securing MCP with OAuth 2.1: Essential Security Practices for Developers
OAuth 2.1 has become the gold standard for authorization in modern applications, but implementing it securely requires careful attention to numerous security considerations. When building Model Context Protocol (MCP) implementations, following OAuth 2.1 security best practices isn't just recommended—it's mandatory for protecting your users and systems from sophisticated attacks.
This comprehensive guide walks through the critical security requirements that every MCP implementation must follow, from token audience validation to preventing confused deputy attacks.
The Foundation: OAuth 2.1 Security Best Practices
Every MCP implementation must strictly adhere to OAuth 2.1 Section 7's security considerations. These aren't suggestions—they're requirements that form the security foundation of your entire system. Cutting corners on these fundamentals can expose your application to token theft, injection attacks, and privilege escalation vulnerabilities.
Token Audience Binding: Your First Line of Defense
One of the most critical yet often overlooked security measures is proper token audience validation. RFC 8707 Resource Indicators provide essential security benefits by ensuring tokens can only be used with their intended resources.
What MCP Clients Must Do:
Include the
resourceparameter in all authorization and token requestsExplicitly specify the target resource when requesting tokens
Never assume tokens are valid for multiple services
What MCP Servers Must Do:
Validate that every token was specifically issued for their use
Reject tokens that don't include them in the audience claim
Verify they are the intended recipient before processing any request
This audience binding prevents attackers from reusing legitimate tokens across different services—a common attack vector that can compromise entire systems.
Protecting Against Token Theft
Stolen tokens represent one of the most dangerous security threats in OAuth implementations. Whether tokens are extracted from client storage, server caches, or application logs, they can grant attackers seemingly legitimate access to protected resources.
Secure Token Storage Requirements:
Implement secure storage mechanisms that protect tokens at rest
Follow OAuth 2.1 Section 7.1 guidelines for token handling
Never store tokens in plaintext or easily accessible locations
Authorization Server Best Practices:
Issue short-lived access tokens to minimize the impact of token compromise
For public clients, implement mandatory refresh token rotation as specified in OAuth 2.1 Section 4.3.1
Monitor for unusual token usage patterns that might indicate theft
Communication Security: HTTPS Everywhere
Network-level security forms the backbone of OAuth security. All OAuth communications must occur over encrypted channels to prevent interception and man-in-the-middle attacks.
Non-Negotiable Requirements:
All authorization server endpoints must use HTTPS
Redirect URIs must either be localhost or use HTTPS
No exceptions for development or testing environments in production
Authorization Code Protection with PKCE
Authorization codes represent a brief but critical window of vulnerability. An attacker who intercepts an authorization code can potentially exchange it for access tokens, compromising the entire authentication flow.
PKCE Implementation Requirements: MCP clients must implement Proof Key for Code Exchange (PKCE) according to OAuth 2.1 Section 7.5.2. PKCE works by requiring clients to:
Generate a cryptographically random code verifier
Create a code challenge derived from the verifier
Include the challenge in the authorization request
Provide the original verifier when exchanging the code for tokens
This mechanism ensures that even if an authorization code is intercepted, it cannot be used without the original code verifier, effectively neutralizing code interception attacks.
Preventing Open Redirection Attacks
Malicious redirect URIs can direct users to phishing sites that steal credentials or install malware. Proper redirect URI validation is essential for maintaining user trust and security.
Client Requirements:
Register all redirect URIs with the authorization server
Use and verify state parameters in authorization code flows
Discard any results that don't match the original state parameter
Authorization Server Requirements:
Validate exact redirect URIs against pre-registered values
Never allow dynamic or partially matched redirect URIs
Only automatically redirect to trusted URIs
Inform users and require explicit consent for untrusted redirections
Solving the Confused Deputy Problem
The confused deputy problem occurs when MCP servers act as intermediaries to third-party APIs, potentially allowing attackers to exploit the server's privileged position. This is particularly dangerous when using stolen authorization codes to obtain access tokens without proper user consent.
Critical Protection Measures:
MCP proxy servers using static client IDs must obtain explicit user consent for each dynamically registered client
Implement robust consent flows before forwarding requests to third-party authorization servers
Never assume that upstream consent applies to downstream services
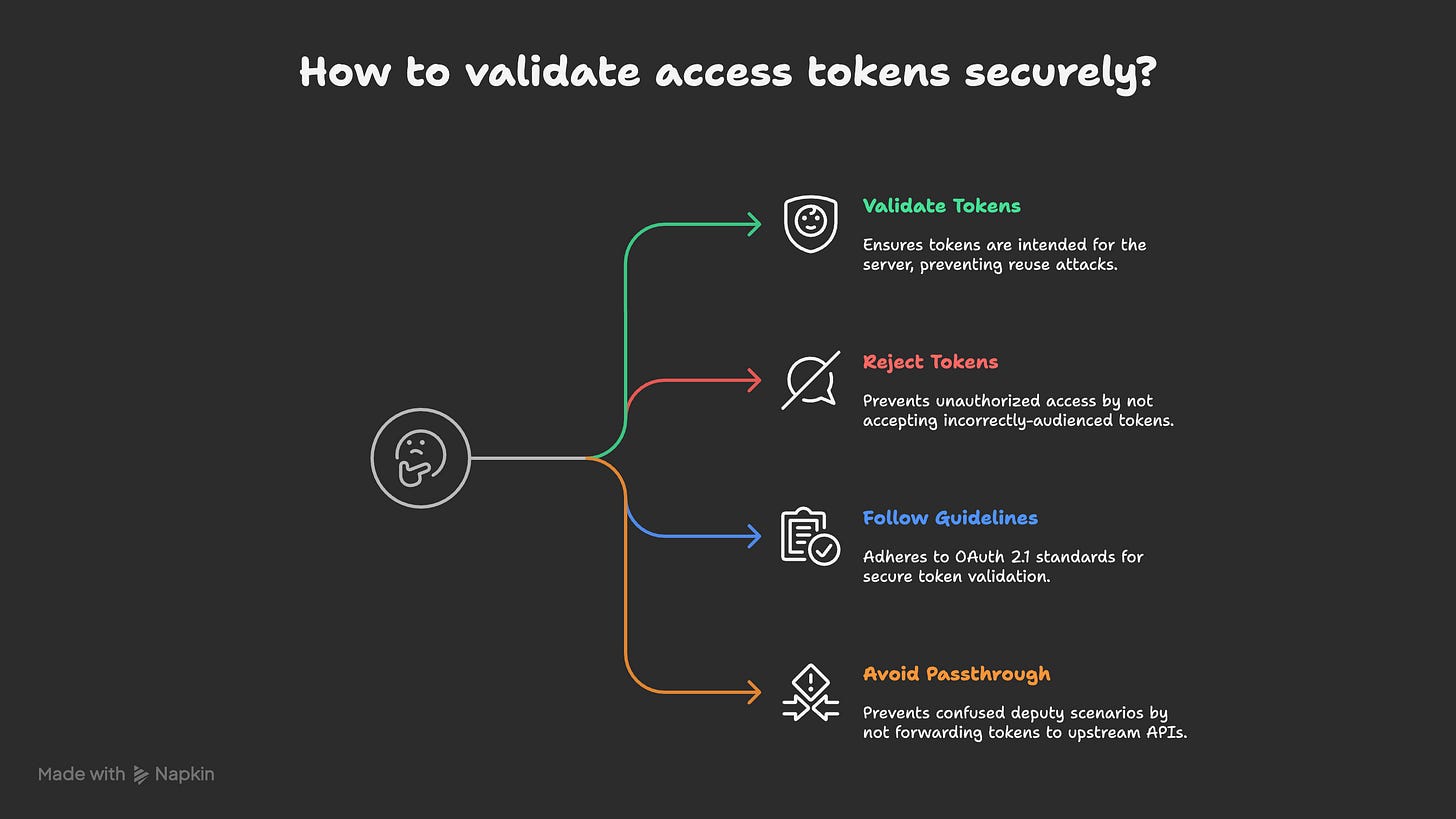
Access Token Privilege Restriction: The Audience Validation Imperative
Improper access token validation represents one of the most severe security vulnerabilities in OAuth implementations. This problem manifests in two critical ways:
Audience Validation Failures: When MCP servers fail to verify that tokens were specifically intended for them, they may accept tokens originally issued for other services. This breaks fundamental OAuth security boundaries and allows token reuse attacks.
Token Passthrough Vulnerabilities: If servers not only accept incorrectly-audienced tokens but also forward them unmodified to downstream services, they create confused deputy scenarios where downstream APIs may incorrectly trust the token's validity.
Mandatory Validation Requirements:
Validate all access tokens before processing requests
Ensure tokens are issued specifically for your MCP server
Follow OAuth 2.1 Section 5.2 guidelines for token validation
Reject tokens that don't include your service in the audience claim
Never pass through tokens received from MCP clients to upstream APIs
Implementing Resource Indicators
MCP clients must implement RFC 8707 Resource Indicators to explicitly specify target resources when requesting tokens. This aligns with RFC 9728 Section 7.4 recommendations and ensures access tokens are properly bound to their intended resources.
Implementation Steps:
Include the
resourceparameter in all token requestsSpecify the exact resource URI for which the token is intended
Validate that received tokens match the requested resource
Implement proper error handling for resource mismatch scenarios
OAuth 2.1 security isn't optional—it's the foundation upon which trustworthy MCP implementations are built. Each security measure outlined here addresses real-world attack vectors that have compromised systems in production environments.
By implementing these security practices from the ground up, you're not just protecting your application—you're contributing to a more secure ecosystem where users can trust that their data and access are properly protected.
Remember: security is not a feature you add later. It's a fundamental requirement that must be baked into every aspect of your OAuth 2.1 and MCP implementation from day one.
If you want to discuss MCP systems with me feel free to drop a mail at subham.kundu@indusxp.com