Securing AI Agents: The Future of MCP Authentication & Authorization
How OAuth 2.1 and token exchange are solving the enterprise AI security challenge
As AI agents like Claude, Cursor, and other intelligent assistants become integral to enterprise workflows, a critical security challenge has emerged: How do we safely allow AI agents to access sensitive enterprise resources on behalf of users?
The Model Context Protocol (MCP) has emerged as a promising standard for AI agent-to-service communication, but with great power comes great security responsibility. Industry experts in OAuth and enterprise security have identified sophisticated authentication and authorization patterns needed to make enterprise AI both powerful and secure.
The Problem: From Local Development to Enterprise Reality
The Naive Approach (Where Most Start)
Many MCP implementations begin with a simple model:
AI client runs locally on user's machine
MCP server also runs locally
Authentication? What authentication?
Downstream API access via hardcoded admin keys or personal access tokens (PATs)
User → AI Client → MCP Server → [Admin API Key] → Downstream Services
This works fine for local development but becomes a security nightmare at enterprise scale. Imagine every employee's AI requests to Dropbox being made with the same admin-level API key!
The Enterprise Reality Check
Real enterprise deployment requires:
Authentication of AI clients to MCP servers
Authorization that respects user permissions and enterprise policies
User-scoped access to downstream services (not admin-level everything)
Audit trails showing who accessed what, when
Standards compliance for security teams
The Solution: OAuth 2.1 + Token Exchange Architecture
The solution leverages battle-tested OAuth patterns with some modern twists designed specifically for AI agent scenarios.
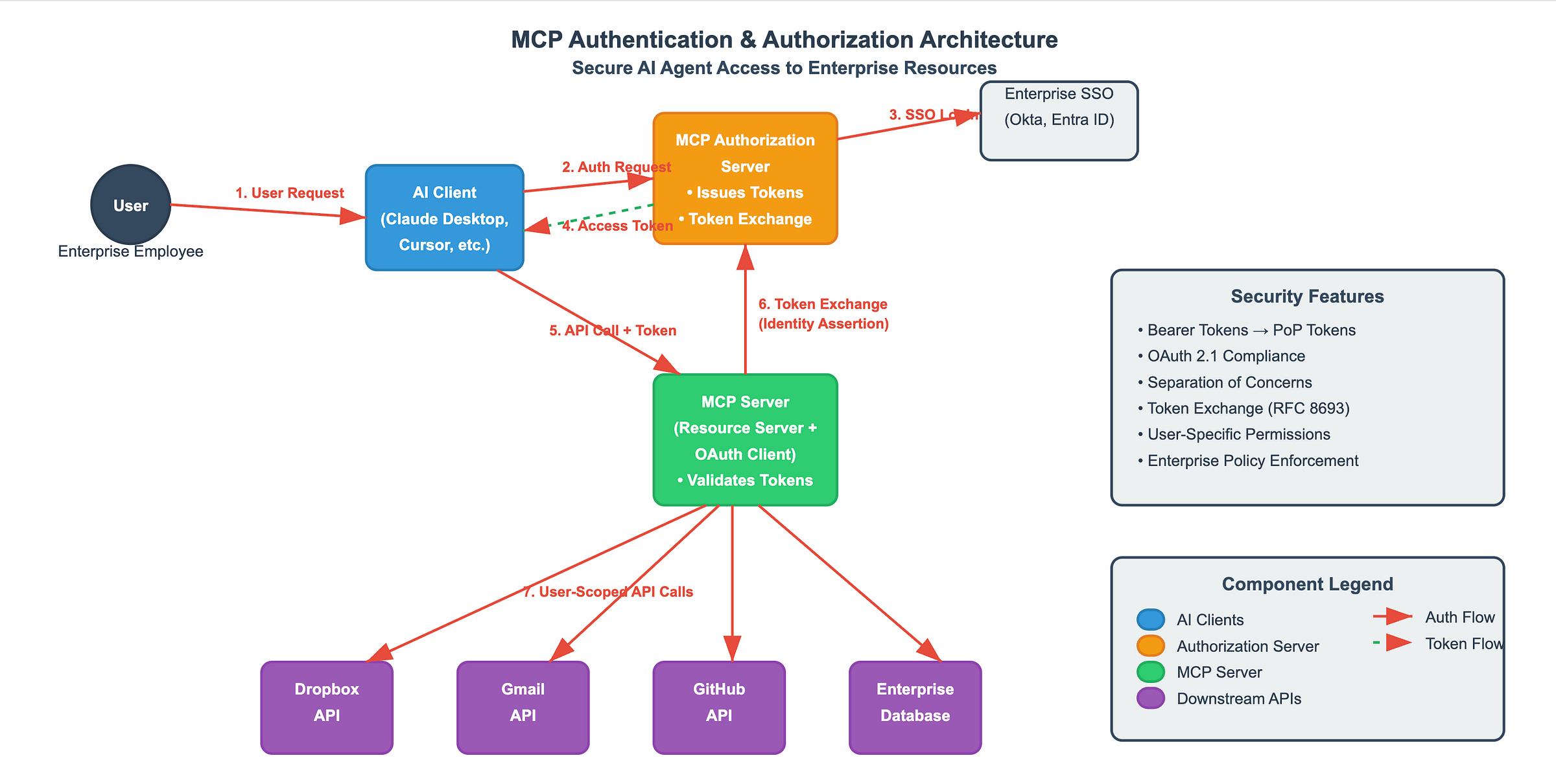
The Three-Layer Architecture
Layer 1: User to AI Client The user interacts with their AI agent (Claude Desktop, Cursor, etc.) as normal. The magic happens behind the scenes.
Layer 2: AI Client to MCP Server ("The First Hop")
AI client redirects user to MCP Authorization Server
User authenticates via enterprise SSO (Okta, Entra ID, etc.)
Authorization server issues access token for MCP server
AI client presents token when calling MCP server
Layer 3: MCP Server to Downstream Services ("The Second Hop")
MCP server receives user's request + valid token
For downstream API calls (Dropbox, Gmail, etc.), MCP server uses Identity Assertion Grant
User's identity token is exchanged for service-specific access tokens
Each downstream call uses appropriate user-scoped permissions
The Token Exchange Magic
The Identity Assertion Grant (RFC 8693) is the secret sauce that makes this architecture elegant:
MCP Server → Authorization Server:
"I have this user's ID token. Please give me a Dropbox token for this specific user."
Authorization Server → MCP Server:
"Here's a user-scoped Dropbox token valid for 1 hour."
This pattern means:
Users authenticate once to their enterprise system
AI clients only need one MCP server token
MCP servers get fresh, scoped tokens for each downstream service
No stored credentials or overly broad permissions
Security Enhancements: Beyond Basic OAuth
From Bearer Tokens to Proof of Possession
Traditional bearer tokens are like hotel key cards - whoever has them can use them. The industry is moving toward Proof of Possession (PoP) tokens that are cryptographically bound to the requesting client.
Bearer Token Risk:
Stolen Token → Immediate unauthorized access
PoP Token Security:
Stolen Token → Useless without cryptographic proof of legitimate client
Separation of Concerns
The architecture cleanly separates responsibilities:
Authorization Server: Issues and manages tokens
MCP Server: Validates tokens and orchestrates downstream access
AI Client: Presents tokens and handles user interaction
Downstream Services: Enforce their own resource protection
Enterprise Benefits: Security Meets User Experience
For Security Teams
Centralized policy enforcement through enterprise SSO
Audit trails showing exactly which AI agents accessed what data
Token lifecycle management with automatic expiration and refresh
Standards compliance with OAuth 2.1 best practices
For End Users
Single sign-on experience - authenticate once, access everything
No credential sharing with individual services
Consistent permissions - AI agents respect the same access controls as direct user access
For Developers
Standard patterns instead of custom auth per integration
Off-the-shelf components rather than building security from scratch
Clear separation between authentication logic and business logic
Implementation Considerations
Current State vs. Future State
MCP Spec Today: Focuses on the "first hop" (client to MCP server authentication)
MCP Spec Tomorrow: Will include standards for the "second hop" (MCP server to downstream services)
Technology Stack Recommendations
OAuth 2.1 as the foundation standard
Identity Assertion Grant for token exchange
Enterprise SSO integration (Okta, Entra ID, etc.)
Proof of Possession tokens for enhanced security
Short-lived tokens with automatic refresh
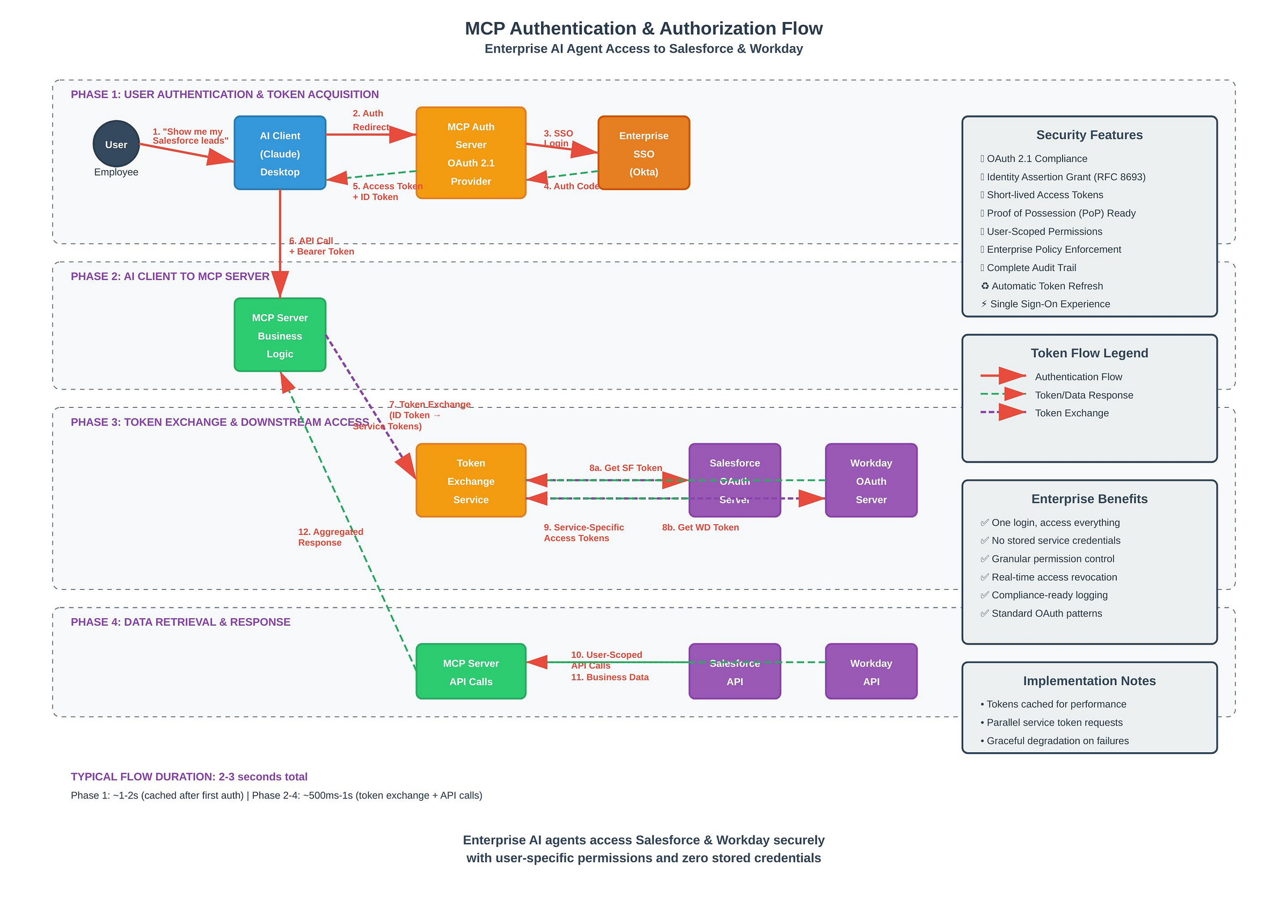
Step-by-Step Implementation: Salesforce & Workday Integration
Let's walk through a practical example of implementing MCP authorization for an enterprise that wants to connect their AI agents to both Salesforce and Workday through a secure MCP server.
Prerequisites
Enterprise OAuth provider (Okta, Entra ID, etc.)
MCP Authorization Server
MCP Server with Salesforce and Workday connectors
AI Client (Claude Desktop, custom enterprise AI app)
User accounts in enterprise SSO, Salesforce, and Workday
Step 1: Configure the MCP Authorization Server
# MCP Authorization Server Configuration
authorization_server:
issuer: "https://mcp-auth.company.com"
# Enterprise SSO Integration
identity_providers:
- name: "company-sso"
type: "okta" # or "entra_id"
client_id: "${COMPANY_SSO_CLIENT_ID}"
client_secret: "${COMPANY_SSO_CLIENT_SECRET}"
discovery_url: "https://company.okta.com/.well-known/openid_configuration"
# Downstream service configurations
token_exchange:
salesforce:
authorization_server: "https://login.salesforce.com"
client_id: "${SALESFORCE_CLIENT_ID}"
client_secret: "${SALESFORCE_CLIENT_SECRET}"
scope: "api refresh_token"
workday:
authorization_server: "https://impl-services1.workday.com/oauth2/company/token"
client_id: "${WORKDAY_CLIENT_ID}"
client_secret: "${WORKDAY_CLIENT_SECRET}"
scope: "Staffing"
Step 2: Register the AI Client
Register your AI client application with the MCP Authorization Server:
POST /oauth2/clients
Content-Type: application/json
Authorization: Bearer ${ADMIN_TOKEN}
{
"client_name": "Enterprise AI Assistant",
"client_type": "public",
"redirect_uris": [
"https://ai-client.company.com/callback"
],
"grant_types": ["authorization_code", "refresh_token"],
"scope": "mcp:server:access profile"
}
Step 3: Configure the MCP Server
// MCP Server Configuration
const mcpServer = new MCPServer({
authorization: {
server_url: "https://mcp-auth.company.com",
audience: "mcp-server",
required_scopes: ["mcp:server:access"]
},
tools: [
{
name: "salesforce-connector",
description: "Access Salesforce CRM data",
required_token_exchange: "salesforce"
},
{
name: "workday-connector",
description: "Access Workday HR data",
required_token_exchange: "workday"
}
]
});
Step 4: Implement the Authentication Flow
Phase 1: User Authentication
// AI Client initiates authentication
const authUrl = `https://mcp-auth.company.com/oauth2/authorize?` +
`client_id=${CLIENT_ID}&` +
`redirect_uri=${REDIRECT_URI}&` +
`response_type=code&` +
`scope=mcp:server:access profile&` +
`state=${CSRF_TOKEN}`;
// Redirect user to authorization server
window.location.href = authUrl;
Phase 2: Token Exchange
// After user authenticates, exchange code for tokens
const tokenResponse = await fetch('https://mcp-auth.company.com/oauth2/token', {
method: 'POST',
headers: { 'Content-Type': 'application/x-www-form-urlencoded' },
body: new URLSearchParams({
grant_type: 'authorization_code',
code: authorizationCode,
client_id: CLIENT_ID,
redirect_uri: REDIRECT_URI
})
});
const { access_token, id_token, refresh_token } = await tokenResponse.json();
Step 5: AI Client to MCP Server Communication
// AI Client calls MCP Server with user's access token
const mcpResponse = await fetch('https://mcp-server.company.com/tools/execute', {
method: 'POST',
headers: {
'Authorization': `Bearer ${access_token}`,
'Content-Type': 'application/json'
},
body: JSON.stringify({
tool: "salesforce-connector",
action: "get_opportunities",
parameters: {
status: "open",
owner: "current_user"
}
})
});
Step 6: MCP Server Token Exchange for Downstream Access
// MCP Server exchanges user's identity for Salesforce-specific token
async function getSalesforceToken(userIdToken) {
const tokenExchangeResponse = await fetch('https://mcp-auth.company.com/oauth2/token', {
method: 'POST',
headers: { 'Content-Type': 'application/x-www-form-urlencoded' },
body: new URLSearchParams({
grant_type: 'urn:ietf:params:oauth:grant-type:token-exchange',
subject_token: userIdToken,
subject_token_type: 'urn:ietf:params:oauth:token-type:id_token',
audience: 'https://login.salesforce.com',
requested_token_type: 'urn:ietf:params:oauth:token-type:access_token'
})
});
const { access_token } = await tokenExchangeResponse.json();
return access_token;
}
// Use the exchanged token for Salesforce API calls
const salesforceResponse = await fetch('https://company.salesforce.com/services/data/v58.0/sobjects/Opportunity', {
headers: {
'Authorization': `Bearer ${salesforceAccessToken}`,
'Content-Type': 'application/json'
}
});
Step 7: Workday Integration (Similar Pattern)
// Token exchange for Workday access
async function getWorkdayToken(userIdToken) {
const tokenExchangeResponse = await fetch('https://mcp-auth.company.com/oauth2/token', {
method: 'POST',
headers: { 'Content-Type': 'application/x-www-form-urlencoded' },
body: new URLSearchParams({
grant_type: 'urn:ietf:params:oauth:grant-type:token-exchange',
subject_token: userIdToken,
subject_token_type: 'urn:ietf:params:oauth:token-type:id_token',
audience: 'https://impl-services1.workday.com',
requested_token_type: 'urn:ietf:params:oauth:token-type:access_token'
})
});
return tokenExchangeResponse.json();
}
// Query Workday for employee data
const workdayResponse = await fetch('https://impl-services1.workday.com/ccx/service/company/Human_Resources/v42.1', {
method: 'POST',
headers: {
'Authorization': `Bearer ${workdayAccessToken}`,
'Content-Type': 'application/soap+xml'
},
body: workdaySOAPRequest
});
Step 8: Error Handling and Token Refresh
// Implement robust error handling
class MCPAuthManager {
async callWithTokenRefresh(apiCall) {
try {
return await apiCall();
} catch (error) {
if (error.status === 401) {
// Token expired, refresh and retry
await this.refreshTokens();
return await apiCall();
}
throw error;
}
}
async refreshTokens() {
const response = await fetch('https://mcp-auth.company.com/oauth2/token', {
method: 'POST',
headers: { 'Content-Type': 'application/x-www-form-urlencoded' },
body: new URLSearchParams({
grant_type: 'refresh_token',
refresh_token: this.refreshToken,
client_id: CLIENT_ID
})
});
const tokens = await response.json();
this.updateStoredTokens(tokens);
}
}
Security Considerations for Implementation
Token Storage: Never store tokens in localStorage - use secure, HTTP-only cookies or encrypted storage
CSRF Protection: Always use state parameters in OAuth flows
Token Expiration: Implement automatic token refresh before expiration
Audit Logging: Log all token exchanges and API calls for compliance
Scope Limitation: Request minimum necessary scopes for each service
Error Handling: Implement graceful degradation when services are unavailable
This implementation provides a complete, production-ready approach to MCP authorization that enables secure AI agent access to enterprise systems while maintaining user privacy and administrative control.
As AI agents become more sophisticated and access increasingly sensitive data, authentication and authorization cannot be an afterthought. The patterns discussed here represent the leading edge of enterprise AI security thinking.
Key trends to watch:
Standardization of MCP auth patterns across the industry
Enhanced token security with widespread PoP adoption
Fine-grained permissions for AI agent actions
Cross-organization federation for multi-tenant AI services
Key Takeaways
OAuth 2.1 is the way forward - Don't reinvent authentication and authorization
Token exchange enables seamless UX - Users authenticate once, access everything securely
Separation of concerns is critical - Authorization servers, resource servers, and clients have distinct roles
Proof of Possession tokens are becoming essential for high-security environments
Enterprise adoption requires audit trails, policy enforcement, and standards compliance
The future of enterprise AI depends on getting security right from the start. The authentication and authorization patterns emerging around MCP provide a roadmap for building AI systems that are both powerful and secure.
If you want to connect with me, please feel free to drop a Hi at Substack or email me at subhamkundu999@gmail.com.